
GRC Cyber Security: A Practical Guide to Governance, Risk & Compliance for Your Security Program
In such an increasingly complicated cyber security climate, businesses are confronted with more obstacles than ever when it comes to safeguarding sensitive data and remaining compliant in the face of continuously changing regulations. If you’re in charge of your company’s cyber security, GRC Cyber Security is a term that has likely come across your radar by now. But what does it really mean? And most importantly, what can it do for you in terms of establishing a foundation to help protect your organization from cyber threats?
In this article, I’m introducing GRC Cyber Security and, breaking down Governance Risk Management & Compliance along with how they combine into a strong cyber security program. You’ll also discover how GRC
Tools, and automation are critical to making it easier to implement and yield a stronger overall security posture.
Quick overview: What is GRC in cyber security?
Short definition + why it matters now
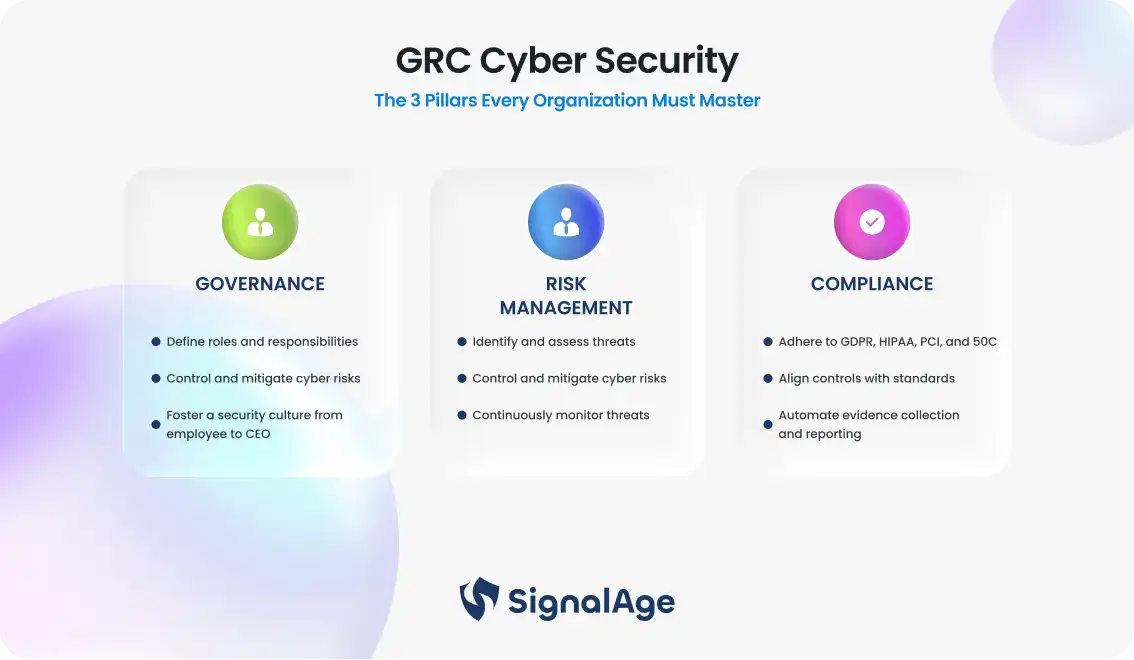
GRC – What Does it Mean for Me? GRC, which denotes Governance, Risk and Compliance encompasses the three crucial pillars that every organization need to address in order to fulfill regulatory standards, remain safe from risk and align themselves with their business objectives. In reality, Governance Risk Compliance Cyber security takes these principles to the next level by focusing on the cyber security specific application of these familiar concepts – making sure that your security policies and processes comply with applicable laws, managing risk well, and translating into sustained compliance.
With the rise of data breaches, and GDRP enforcement increasing the focus on cyber security at a global scale, awareness for organizations to manage their risk has never been higher. Without a robust GRC strategy, enterprises are susceptible to non-compliance, loss of brand and huge financial impact due to cybersecurity attacks.
Core components: Governance, Risk Management, Compliance
Governance: roles, policies, and oversight
When you say governance with GRC Cyber, it means the roles, policies, and oversight that makes cyber security line up with your organization’s needs and regulations.
This includes setting out clear roles, ensuring that the right people make decisions and providing a framework to ensure leaders are held accountable and policies are transparent.
Strong governance means a security-oriented culture permeates the organization, from IT staff to the executive suite, so each person understands their contribution to protecting company data.
Compliance: mapping controls to regulations (GDPR, HIPAA, PCI, SOC2)
Compliance is a critical part of GRC Cyber Security. But failing to live up to the rules set out by regulations like GDPR, HIPAA, PCI-DSS, and SOC2 can land an organization with some serious penalties and a blow to their reputation. Compliance mapping is all about lining up your security controls to fit in with what the regulators are asking for, so you can prove to them that you’re playing by the book.
Getting your hands on some compliance automation software can make all the difference, by taking a lot of the hard work out of things like collecting evidence, testing controls and doing audits.
Common GRC frameworks & when to use them
GRC Cyber Security is not an off-the-shelf solution. Every industry and regulatory environment has its needs. In this article, we will look in detail at some of the commonly used GRC frameworks and when one should apply them.
NIST CSF / NIST 2.0 (mapping + strengths)
NIST CSF is the go to framework for many in the public and private sectors who want to improve their cyber security. It’s a flexible, risk-based approach that focuses on key areas like Identify, Protect, Detect, Respond, and Recover. A lot of organizations find that NIST CSF offers more flexibility than ISO 27001 when it comes to putting it into practice. If you’re looking for a framework that most people know and respect and that you can use across different industries then NIST CSF is a good fit.
ISO 27001 / ISO 27002
ISO 27001 provides some of the best practices for running an ISMS, or information security management system. It helps you protect data from being compromised. It’s one of the most widely recognized GRC frameworks globally which makes it a good choice if your organization needs to meet pretty tough data protection requirements.
SOC2 / HIPAA / CMMC / ISO 31000
Other GRC frameworks, on the other hand, are more focused on particular industries, and they are SOC2, HIPAA, CMMC, and ISO 31000. They provide you with clear guidelines on how to protect sensitive data and achieve the regulatory requirements of your sector, whether in healthcare, defense, or other general risk management.
GRC tooling & automation: What to look for
To make your GRC processes run smoothly, you need to invest in some good GRC tools and software. Modern GRC platforms help you map your GRC frameworks, automate evidence collection, and track compliance metrics without breaking a sweat.
Continuous monitoring & integrations (SIEM, IAM, CMDB)
It is also a good idea to get some continuous monitoring tools in place, such as SIEM, IAM, and CMDB, as part of your overall GRC Cyber strategy. These tools provide real-time visibility into your security posture and can trigger alerts when your security controls fail or a breach is detected.
Step-by-step implementation roadmap
Implementing a GRC Cyber Security program can sound daunting; it does not have to be overwhelming. If you’re looking to get started, here’s a straightforward step-by-step roadmap to follow:
Assess → Design → Implement controls → Automate evidence → Monitor & improve
First, take a hard look at where your organization currently stands with regard to Cyber Security. Then, design some policies and procedures to plug any gaps you find. Next up, put in place the necessary controls – firewalls, access restrictions, etc. – and start making it easier to collect evidence for compliance reports by automating the process where you can. Finally, keep a close eye on your program and make improvements as you go along – based both on the results of any audits and the ever-changing threat landscape.
Many organizations partner with cybersecurity consulting teams to design policies, validate controls, and build a scalable GRC roadmap. Businesses in Irvine can achieve the same results with SignalAge’s reliable managed IT services in Irvine, ensuring both regulatory compliance and cyber resilience.
KPIs & Metrics to measure GRC effectiveness
To get a good idea of how well your GRC Cyber program is doing, keep a close eye on a few key performance indicators (KPIs). You might want to refer back to a well-organized GRC checklist and track things like:
- Control coverage %:
How many of your security controls do you have in place to manage the risks you’ve identified – and are they doing the job?
- Time-to-evidence:
How long does it take to get the evidence you need for compliance reporting?
- Audit findings open/closed:
How many audit findings are still outstanding – and how quickly are you closing them down?
- Residual risk score:
After you’ve implemented all the mitigations you can – how much risk are you still left with?
Common pitfalls & how to avoid them
Be wary of these common pitfalls when implementing GRC Cyber:
Soloed teams, lack of executive buy-in, over-reliance on manual evidence collection
- Departmental silos can impede communication, making management of risk across departments more problematic.
- Lack of executive buy-in can stall GRC initiatives when leadership is not fully committed.
- Over-reliance on manual evidence collection is a potential leading cause of inefficiencies and errors. Automate what you can!
Case study / Before & After
Let’s look at a Fitch company that adopted a comprehensive GRC Cyber program. Prior to the implementation of the program, they struggled with manual compliance reporting and missed several key audits. Following the automation of the GRC platform, they saw a reduction in audit time by 40%, while compliance tracking became more effective and efficient, saving both time and money.
GRC Final Word
Ready to implement GRC Cyber Security in your organization? Request a free Cloud Demo or get a GRC Assessment today!
Contact us now for signalage to take the next step in securing your organization.
This article will give a practical, realistic look at GRC Cyber and demonstrate valuable ways in which organizations can streamline their governance, risk management, and compliance processes to keep themselves secure and compliant in the modern digital world.
GRC FAQs:
- What is the GRC Cyber Security framework?
The GRC Cyber Security framework is used for aligning the cybersecurity best practices and regulatory requirements with the governance, risk management, and compliance efforts of organizations.
- How do I implement GRC in my organization?
To implement GRC Cyber Security, assess the present security posture of your organization; then comes designing policies, implementation of controls, automation of evidence collection, and continuous system monitoring.
- What tools are needed for GRC Cyber Security?
General GRC tools include control mapping platforms, evidence collection, and workflow automation. Continuous monitoring using SIEM, IAM, and CMDB is also something to consider.